Kind of in line with my previous post of bulk adding DNS zones and configuring secondaries is the need to bind multiple new host headers to a customer's site. Doing it from the IIS Manager is tedious, to say the least.
Fortunately, there is a way to bulk do this as well. This method is a little clunky, but still way better than doing it all manually.
1. From IIS Manager, locate the identifier for your website (if it's not the default site).
2. Open a command prompt and navigate to (default) \Inetpub\Adminscripts.
3. Run the following command:
cscript adsutil.vbs get w3svc/{site identifier}/serverbindings
The reason this has to be done is the adsutil.vbs set command will overwrite this settings (not add to them), so if you just plug in your new host headers, you'll lose all of your old ones!
You should get an output that looks similar to this:
":80:www.oldhostheader1.com"
":80:www.oldhostheader2.com"
4. Copy/paste the output into a notepad window. Delete the white spaces until it's all one continuous line.
5. Using the same format, add your new host headers to this list so that it looks like this:
":80:www.oldhostheader1.com" ":80:www.oldhostheader2.com" ":80:www.newhostheader1.com" ":80:www.newhostheader2.com"
6. At the beginning of the line, prepend cscript adsutil.vbs set w3svc/{siteidentifier}/server bindings, and save it as a .bat file.
7. Run.
Thursday, December 16, 2010
Quick 'n dirty DNSCMD scripts
Periodically, I get requests to bulk add domains to our DNS hosting environment. Here are a few simple DNScmd scripts to help make the job easier.
On the DNS Primary server, I created a batch script named "zoneadd_primary.bat" and put this in it:
@ECHO OFF
REM
REM Add DNS zones in from command line parameter file as
REM Standard Primary zones.
REM Replace n.n.n.n with IP address of primary/master DNSserver.
REM Replace x.x.x.x and y.y.y.y with your secondary/slave servers.
REM Check for command-line parameter
if "%1"=="" GOTO USAGE
for /F %%a in (%1) do dnscmd /zoneadd %%a /primary /file %%a.dns
REM Add secondary/slave servers to zones
for /F %%a in (%1) do dnscmd /zoneresetsecondaries %%a /securelist x.x.x.x y.y.y.y
GOTO END
:USAGE
ECHO.
ECHO Error: no file specified
ECHO.
ECHO Usage:
ECHO zoneadd_primary [filename]
ECHO.
ECHO where [filename] is a text file with a list of domains.
ECHO.
ECHO Example:
ECHO.
ECHO zoneadd_primary domains.txt
ECHO.
:END
And then, on the slave servers, I put a companion script called "zoneadd_secondary.bat" with a similar script:
@ECHO OFF
REM
REM Add DNS zones in domains.txt as secondary zones.
REM Replace n.n.n.n with IP address of primary/master server.
if "%1"=="" GOTO USAGE
for /F %%a in (%1) do do dnscmd /zoneadd %%a /secondary n.n.n.n
GOTO END
:USAGE
ECHO.
ECHO Error: no file specified
ECHO.
ECHO Usage:
ECHO zoneadd_secondary [filename]
ECHO.
ECHO where [filename] is a text file with a list of domains.
ECHO.
ECHO Example:
ECHO.
ECHO zoneadd_secondary domains.txt
ECHO.
:END
Not much to it, but I do find it useful.
On the DNS Primary server, I created a batch script named "zoneadd_primary.bat" and put this in it:
@ECHO OFF
REM
REM Add DNS zones in from command line parameter file as
REM Standard Primary zones.
REM Replace n.n.n.n with IP address of primary/master DNSserver.
REM Replace x.x.x.x and y.y.y.y with your secondary/slave servers.
REM Check for command-line parameter
if "%1"=="" GOTO USAGE
for /F %%a in (%1) do dnscmd /zoneadd %%a /primary /file %%a.dns
REM Add secondary/slave servers to zones
for /F %%a in (%1) do dnscmd /zoneresetsecondaries %%a /securelist x.x.x.x y.y.y.y
GOTO END
:USAGE
ECHO.
ECHO Error: no file specified
ECHO.
ECHO Usage:
ECHO zoneadd_primary [filename]
ECHO.
ECHO where [filename] is a text file with a list of domains.
ECHO.
ECHO Example:
ECHO.
ECHO zoneadd_primary domains.txt
ECHO.
:END
And then, on the slave servers, I put a companion script called "zoneadd_secondary.bat" with a similar script:
@ECHO OFF
REM
REM Add DNS zones in domains.txt as secondary zones.
REM Replace n.n.n.n with IP address of primary/master server.
if "%1"=="" GOTO USAGE
for /F %%a in (%1) do do dnscmd /zoneadd %%a /secondary n.n.n.n
GOTO END
:USAGE
ECHO.
ECHO Error: no file specified
ECHO.
ECHO Usage:
ECHO zoneadd_secondary [filename]
ECHO.
ECHO where [filename] is a text file with a list of domains.
ECHO.
ECHO Example:
ECHO.
ECHO zoneadd_secondary domains.txt
ECHO.
:END
Not much to it, but I do find it useful.
Saturday, December 11, 2010
Mitch McConnell, This One's For You
Also titled, "Everything that's wrong with Republicans and Democrats."
It's been a while since I've posted something political; now that the dust is getting kicked up around the compromise deal between President Obama and the Senate Republicans, I think it's a good time to let my feelings out.
Hearing Mitch McConnell on the radio is an audio reminder of why I don't consider myself a Republican anymore. I have no idea how he can claim that extending the Bush tax cuts to the wealthiest 2% of Americans is going to help our ailing economy. Since it's obvious that it's been a few years since he's had an economics course, I'm going to share my limited recollection of college econ.
Now, mind you, I was born and raised in a house that bled Reaganomics. I still hear stories about how I ran around the Whitewater Armory on election day yelling "Ronald Reagan is a good man!" I was always told that the rich people create jobs and that you never asked a Wal-Mart greeter for a job. I was told that everyone's born a Democrat, and then they grow up.
However, I've come to the realization that this particular viewpoint was very one-sided and not very practical.
While rich people and businss owners *do* create jobs, they create jobs when there is sufficient economic cause to do so. Rich people didn't get to be rich by spending their money foolishly, and few things are more foolish than employing a bunch of people making stuff that isn't getting sold.
For some reason, Mitch McConnel seems sold on the idea that the richest 2% of Americans need all of these tax breaks extended because we're in a fragile economy and that extra oomph is needed to entice them to create jobs.
Mitch, I've got news for you--no one with bags of money sits around thinking, "I'm going to create some jobs by employing a bunch of minimum wage folks in hopes of stimulating the economy." There is no benevolent employer who is looking for the opportunity to create a warehouse full of unsold goods. Rich people don't get to be rich by hiring a bunch of people to stand around idle. What stimulates the economy is a lot of people buying stuff over a sustained period. The spending must come before the job creation does.
What he (and the other Congressional Republicans) need to remember is that the most direct ways to stimulate the economy and reduce the deficit are:
1. Extend unemployment benefits. People who are on unemployment aren't building a rainy day fund. UE is barely enough to keep food on the table for most families; every last penny of it is going immediately back into the economy.
2. Simplify the tax structure. It was tried in 1986, but didn't really have a huge net change. There are so many loopholes favoring the rich that they can, in some cases, pay less taxes than people making 1/10 of what they make. Eliminate the vast majority of deductions. There is no reason that the personal tax code can't be under 100 pages, or even 50.
3. Broaden the tax base. Get more people to pay taxes. Fewer exemptions and deductions means more people are affected.
4. Lower marginal tax rates. If the tax base is sufficiently broad, everyone's marginal rates can go down. This woul directly put money back into pockets to be spent. A family of four making $40,000 per year spends a much higher percentage of their income on necessities than a single person making $2m a year. Lowering the tax rates (especially on the low end of the income scale) again means that more money would be going directly back into the economy. And we all know that money flowing in means employers need to hire more people (that whole supply and demand thing).
The President and his Debt Commission have several recommendations; I think a lot of the ideas are good. There are only two ways to shrink the deficit--raise revenues and cut spending. Republicans and Democrats seem to think that those ideas are mutually exclusive. Democrats want to increase revenues, Republicans want to cut spending on bleeding-heart programs.
Things that I think would beneficial for a comprehensive tax plan:
1. Exempt first $35,000 from personal income tax.
2. Do away with all deductions except charity and medical expenses (EIC, mortgage deduction, etc)
3. Eliminate capital gains tax.
4. Eliminate inheritance tax.
5. Implement progressive income tax (maybe about 18% on $35,000-70,000; 22% on $70,000-150,000; 25% on 150,000-$500,000, etc. It would take a bit of math, but in the end, the marginal tax rates drop significantly, but with a broader base and only two deductions (charity and medical expenses), I think we'd see an overall increase in government revenue.
My numbers may need some tweaking, but I think in teh end, it's going to take some out-of-the-box ideas like that (like touching the sacred cow "Mortgage deduction") to put real money back in the pockets of the people most likely to spend it and start growing our economy.
It's been a while since I've posted something political; now that the dust is getting kicked up around the compromise deal between President Obama and the Senate Republicans, I think it's a good time to let my feelings out.
Hearing Mitch McConnell on the radio is an audio reminder of why I don't consider myself a Republican anymore. I have no idea how he can claim that extending the Bush tax cuts to the wealthiest 2% of Americans is going to help our ailing economy. Since it's obvious that it's been a few years since he's had an economics course, I'm going to share my limited recollection of college econ.
Now, mind you, I was born and raised in a house that bled Reaganomics. I still hear stories about how I ran around the Whitewater Armory on election day yelling "Ronald Reagan is a good man!" I was always told that the rich people create jobs and that you never asked a Wal-Mart greeter for a job. I was told that everyone's born a Democrat, and then they grow up.
However, I've come to the realization that this particular viewpoint was very one-sided and not very practical.
While rich people and businss owners *do* create jobs, they create jobs when there is sufficient economic cause to do so. Rich people didn't get to be rich by spending their money foolishly, and few things are more foolish than employing a bunch of people making stuff that isn't getting sold.
For some reason, Mitch McConnel seems sold on the idea that the richest 2% of Americans need all of these tax breaks extended because we're in a fragile economy and that extra oomph is needed to entice them to create jobs.
Mitch, I've got news for you--no one with bags of money sits around thinking, "I'm going to create some jobs by employing a bunch of minimum wage folks in hopes of stimulating the economy." There is no benevolent employer who is looking for the opportunity to create a warehouse full of unsold goods. Rich people don't get to be rich by hiring a bunch of people to stand around idle. What stimulates the economy is a lot of people buying stuff over a sustained period. The spending must come before the job creation does.
What he (and the other Congressional Republicans) need to remember is that the most direct ways to stimulate the economy and reduce the deficit are:
1. Extend unemployment benefits. People who are on unemployment aren't building a rainy day fund. UE is barely enough to keep food on the table for most families; every last penny of it is going immediately back into the economy.
2. Simplify the tax structure. It was tried in 1986, but didn't really have a huge net change. There are so many loopholes favoring the rich that they can, in some cases, pay less taxes than people making 1/10 of what they make. Eliminate the vast majority of deductions. There is no reason that the personal tax code can't be under 100 pages, or even 50.
3. Broaden the tax base. Get more people to pay taxes. Fewer exemptions and deductions means more people are affected.
4. Lower marginal tax rates. If the tax base is sufficiently broad, everyone's marginal rates can go down. This woul directly put money back into pockets to be spent. A family of four making $40,000 per year spends a much higher percentage of their income on necessities than a single person making $2m a year. Lowering the tax rates (especially on the low end of the income scale) again means that more money would be going directly back into the economy. And we all know that money flowing in means employers need to hire more people (that whole supply and demand thing).
The President and his Debt Commission have several recommendations; I think a lot of the ideas are good. There are only two ways to shrink the deficit--raise revenues and cut spending. Republicans and Democrats seem to think that those ideas are mutually exclusive. Democrats want to increase revenues, Republicans want to cut spending on bleeding-heart programs.
Things that I think would beneficial for a comprehensive tax plan:
1. Exempt first $35,000 from personal income tax.
2. Do away with all deductions except charity and medical expenses (EIC, mortgage deduction, etc)
3. Eliminate capital gains tax.
4. Eliminate inheritance tax.
5. Implement progressive income tax (maybe about 18% on $35,000-70,000; 22% on $70,000-150,000; 25% on 150,000-$500,000, etc. It would take a bit of math, but in the end, the marginal tax rates drop significantly, but with a broader base and only two deductions (charity and medical expenses), I think we'd see an overall increase in government revenue.
My numbers may need some tweaking, but I think in teh end, it's going to take some out-of-the-box ideas like that (like touching the sacred cow "Mortgage deduction") to put real money back in the pockets of the people most likely to spend it and start growing our economy.
Thursday, December 9, 2010
How to Join Windows XP Media Center to a Domain
During an SBS deployment, I ran into a few machines at my customer's site that were running Windows XP Media Center Edition (MCE). As most of you know, the only machines that are technically eligible to join a Windows domain are "Business" class operating systems, such as Windows XP Professional, Windows Vista Business, Windows Vista Enterprise, Windows 7 Professional and Windows 7 Enterprise (although not technically "business" class, Windows Vista/7 Ultimate Editions are also able to join domains, since they're supposed to be everything-but-the-kitchen-sink editions).
And, as luck would have it, the customer has critical LOB applications installed on these machines and some other pieces of legacy software for which the media is no where to be found, so a fresh install with Windows XP Professional media is out of the question.
No problem, right? I've upgraded dozens of Windows XP Home PCs to Windows XP Professional for this exact reason. I pop some newly acquired Windows XP Professional with SP3 "Get Genuine" media (designed for those folks that have potentially illegitimate Windows versions); the upgrade is going well until ... the part where I enter the license key. It won't take it, even though I know it's valid (tested against an XP Home machine in the same office).
While trying to find a reason why I can't upgrade, I stumble upon another blog with some basic instructions on how to join XP MCE to a domain. The first step the author lists is to install the Windows XP Recovery Console; I run the command and restart ... and ... bluescreen.
I turn to my trusty recovery tools disc (which has gotten me out of more tight spots than you can imagine) and boot to a WinPE shell which has a bunch of great tools loaded, including RegEdit PE.
To perform this feat of amazement yourself:
1. From a WinPE installation, launch RegEdit PE, point it to the Windows installation director, and load up the registry hives.
2. Navigate to HKEY_LOCAL_MACHINE\_REMOTE_SYSTEM\WPA\MedCtrUpg.
3. Double-click the value IsLegacyMCE.
4. Change the '0' to a '1'.
5. Close RegEdit PE and restart the machine into Windows.
6. Join domain.
And, as luck would have it, the customer has critical LOB applications installed on these machines and some other pieces of legacy software for which the media is no where to be found, so a fresh install with Windows XP Professional media is out of the question.
No problem, right? I've upgraded dozens of Windows XP Home PCs to Windows XP Professional for this exact reason. I pop some newly acquired Windows XP Professional with SP3 "Get Genuine" media (designed for those folks that have potentially illegitimate Windows versions); the upgrade is going well until ... the part where I enter the license key. It won't take it, even though I know it's valid (tested against an XP Home machine in the same office).
While trying to find a reason why I can't upgrade, I stumble upon another blog with some basic instructions on how to join XP MCE to a domain. The first step the author lists is to install the Windows XP Recovery Console; I run the command and restart ... and ... bluescreen.
I turn to my trusty recovery tools disc (which has gotten me out of more tight spots than you can imagine) and boot to a WinPE shell which has a bunch of great tools loaded, including RegEdit PE.
To perform this feat of amazement yourself:
1. From a WinPE installation, launch RegEdit PE, point it to the Windows installation director, and load up the registry hives.
2. Navigate to HKEY_LOCAL_MACHINE\_REMOTE_SYSTEM\WPA\MedCtrUpg.
3. Double-click the value IsLegacyMCE.
4. Change the '0' to a '1'.
5. Close RegEdit PE and restart the machine into Windows.
6. Join domain.
Friday, November 5, 2010
Outlook Anywhere and Wildcard Certificates in Exchange 2010
When migrating to a new Exchange 2010 environment, I decided to use a wildcard certificate instead of a UC certificate. It cost about twice as much, but seeing as how I have several other services that currently require SSL certificates, it seemed like a good investment.
When running through the Exchange Remote Connectivity Analyzer, I noticed that my configuration kept failing the Outlook Anywhere test with the following error:
Testing SSL mutual authentication with the RPC proxy server.
Verification of mutual authentication failed.
> Additional Details
>> The certificate common name *.domain.com doesn't validate against the mutual authentication that was provided: msstd:mail.domain.com
The solution was relatively easy. Log into your Exchange CAS server and run the following cmdlet from the Exchange Command Shell:
Set-OutlookProvider -Identity EXPR -CertPrincipalName *.domain.com
I've seen some documentation that replaced the CertPrincipalName value with msstd:*.domain.com, but I believe that is incorrect. The name on the actual SSL certificate is *.domain.com, not msstd:*.domain.com. For giggles, I did try using msstd:*.domain.com as the CertPrincipalName value, but it did not allow me to pass ExRCA.
Run the Get-OutlookProvider cmdlet to review your settings:
RunspaceId : 841d7d59-e89c-42b4-9c3c-9388d40dcd95
CertPrincipalName : *.domain.com
Server :
TTL : 1
OutlookProviderFlags : None
AdminDisplayName :
ExchangeVersion : 0.1 (8.0.535.0)
Name : EXPR
DistinguishedName : CN=EXPR,CN=Outlook,CN=AutoDiscover,CN=Client Access,CN=A
pex Digital Solutions,CN=Microsoft Exchange,CN=Services,
CN=Configuration,DC=domain,DC=com
Identity : EXPR
Guid : d81b1280-1843-4808-812c-48375ed744e0
ObjectCategory : domain.com/Configuration/Schema/ms-Exch-Auto-Discove
r-Config
ObjectClass : {top, msExchAutoDiscoverConfig}
WhenChanged : 11/5/2010 11:53:39 AM
WhenCreated : 1/30/2009 9:23:30 PM
WhenChangedUTC : 11/5/2010 3:53:39 PM
WhenCreatedUTC : 1/31/2009 2:23:30 AM
OrganizationId :
OriginatingServer : mydc03.domain.com
IsValid : True
When running through the Exchange Remote Connectivity Analyzer, I noticed that my configuration kept failing the Outlook Anywhere test with the following error:
Testing SSL mutual authentication with the RPC proxy server.
Verification of mutual authentication failed.
> Additional Details
>> The certificate common name *.domain.com doesn't validate against the mutual authentication that was provided: msstd:mail.domain.com
The solution was relatively easy. Log into your Exchange CAS server and run the following cmdlet from the Exchange Command Shell:
Set-OutlookProvider -Identity EXPR -CertPrincipalName *.domain.com
I've seen some documentation that replaced the CertPrincipalName value with msstd:*.domain.com, but I believe that is incorrect. The name on the actual SSL certificate is *.domain.com, not msstd:*.domain.com. For giggles, I did try using msstd:*.domain.com as the CertPrincipalName value, but it did not allow me to pass ExRCA.
Run the Get-OutlookProvider cmdlet to review your settings:
RunspaceId : 841d7d59-e89c-42b4-9c3c-9388d40dcd95
CertPrincipalName : *.domain.com
Server :
TTL : 1
OutlookProviderFlags : None
AdminDisplayName :
ExchangeVersion : 0.1 (8.0.535.0)
Name : EXPR
DistinguishedName : CN=EXPR,CN=Outlook,CN=AutoDiscover,CN=Client Access,CN=A
pex Digital Solutions,CN=Microsoft Exchange,CN=Services,
CN=Configuration,DC=domain,DC=com
Identity : EXPR
Guid : d81b1280-1843-4808-812c-48375ed744e0
ObjectCategory : domain.com/Configuration/Schema/ms-Exch-Auto-Discove
r-Config
ObjectClass : {top, msExchAutoDiscoverConfig}
WhenChanged : 11/5/2010 11:53:39 AM
WhenCreated : 1/30/2009 9:23:30 PM
WhenChangedUTC : 11/5/2010 3:53:39 PM
WhenCreatedUTC : 1/31/2009 2:23:30 AM
OrganizationId :
OriginatingServer : mydc03.domain.com
IsValid : True
Topics:
exchange 2010,
outlook,
ssl,
troubleshooting,
wildcard
Thursday, November 4, 2010
Fun with PIX, Part Deux
After getting my PIX to boot in my previous post, I decided to run through the password recovery procedures.
What you'll need:
What you'll need:
- PIX recovery images (availble from either the Cisco site individually or here in one ZIP file)
- PIX firewall software version
- TFTP server software (I used the TFTP server included in the PacketTrap pt360 Suite in this exercise)
- Terminal Emulator (I typically use PuTTY)
Steps:
- Connect Ethernet 0 on the PIX to your local LAN.
- Open a command prompt and run ipconfig to determine your computer's IP address.
- Download PIX recovery images to a directory on your computer (such as C:\tftp).
- Point your TFTP server to the download directory containing your tools.
- With a console cable attached and terminal emulator running, power on the PIX firewall.
- Note the version of the PIX firewall software. If you missed the boot sequence, you can type sh ver at the prompt. The firewall software version will normally be the first line returned:
Cisco PIX Firewall Version 6.3(5)
Cisco PIX Device Manager Version 3.0(4)
In this case, the number you need is "Cisco PIX Firewall Version." - Power off the PIX.
- Power on the PIX.
- After the startup messages appear, press ESC or send a BREAK command. Note: If you do it too early, you'll get a testing/diagnostic menu. To continue the boot process, type C. A successful BREAK command should leave you at the monitor> prompt.
- Type int e0 and press ENTER.
- Type addr a.b.c.d and press ENTER (where a.b.c.d is an IP address you want to assign to the PIX. To reduce troubleshooting, choose an address on the same network as your the computer you're using).
- Type server w.x.y.z and press ENTER (where w.x.y.z is the IP address of the computer you're using to perform this procedure).
- Type file np[nn].bin (where [nn] is the version number corresponding to the BIN file for password recovery. For example, if your PIX is running version 6.3 of the firewall software, enter np63.bin).
- Type tftp and press ENTER.
- When prompted, type Y to erase the passwords.
- If prompted to remove the commands from the configuration, type Y.
- The device will reboot and will have a blank password.
Fun with PIX, Part I
When meeting with a potential customer the other day, she mentioned that she had a running PIX with an unknown password.
I thought I'd refresh my PIX skills and decided to bust out an old PIX 506E we had sitting in the office. After the unfortunate re-realization that my laptop doesn't have a serial port (and the resulting short jaunt to the computer store to get a USB-to-Serial cable), I consoled into the PIX and turned it on.
My adventure was short-lived, however. While watching the boot-up, I was greeted with a hung firewall:
CISCO SYSTEMS PIX FIREWALL
Embedded BIOS Version 4.3.207 01/02/02 16:12:22.73
Compiled by morlee
32 MB RAM
PCI Device Table.
Bus Dev Func VendID DevID Class Irq
00 00 00 8086 7192 Host Bridge
00 07 00 8086 7110 ISA Bridge
00 07 01 8086 7111 IDE Controller
00 07 02 8086 7112 Serial Bus 9
00 07 03 8086 7113 PCI Bridge
00 0D 00 8086 1209 Ethernet 11
00 0E 00 8086 1209 Ethernet 10
And that's all she wrote.

3. Locate the J5 jumper. It should be right next to the CMOS battery. Move it over 1 PIN.

4. Power on the device.
5. After unit has booted, power off.
6. Replace cover.
I thought I'd refresh my PIX skills and decided to bust out an old PIX 506E we had sitting in the office. After the unfortunate re-realization that my laptop doesn't have a serial port (and the resulting short jaunt to the computer store to get a USB-to-Serial cable), I consoled into the PIX and turned it on.
My adventure was short-lived, however. While watching the boot-up, I was greeted with a hung firewall:
CISCO SYSTEMS PIX FIREWALL
Embedded BIOS Version 4.3.207 01/02/02 16:12:22.73
Compiled by morlee
32 MB RAM
PCI Device Table.
Bus Dev Func VendID DevID Class Irq
00 00 00 8086 7192 Host Bridge
00 07 00 8086 7110 ISA Bridge
00 07 01 8086 7111 IDE Controller
00 07 02 8086 7112 Serial Bus 9
00 07 03 8086 7113 PCI Bridge
00 0D 00 8086 1209 Ethernet 11
00 0E 00 8086 1209 Ethernet 10
And that's all she wrote.
Fortunately, there's an easy enough work-around.
1. Power off the device.
2. Remove the cover. There are two Phillips screws located at the top rear of the unit. The top half slides back about an inch or so and then lifts off.

3. Locate the J5 jumper. It should be right next to the CMOS battery. Move it over 1 PIN.

4. Power on the device.
5. After unit has booted, power off.
6. Replace cover.
Wednesday, October 6, 2010
"Saved-Critical" for Almost-Clustered Virtual Machines in Windows 2008 R2 Hyper-V
While staging a clustered Hyper-V environment this week, I ran into a head-scratching issue. After provisioning a few LUNs, masking them, and adding them as available storage to Failover Clustering, I began setting up the virtual machines on one of my cluster nodes. During maintenance, the physical servers were restarted. When I went back to continue configuring the virtual machines (which were not yet clustered at this point), I connected to the physical host on which I had been configuring them. While my other clustered virtual machines were running fine, the new ones that I had not yet finished configuring were in a "Saved-Critical" state.
I attempted to start them, but received an eror that the saved state could not be restored. I attempted to delete the saved state, but received an "Unable to perform operation" error. Additionally, I could not view the properties of the virtual machines in the Saved-Critical state.
I opened up Failover Cluster manager and noticed that the storage was now owned by the other cluster node. The problem is now obvious--the storage is no longer being presented to the host on which I was configuring the virtual machines. So, how to move these disks? Since the disks are marked "Available" (not having run through the new service Failover Clustering wizard to make the virtual machines highly available), I can't move them by right-clicking on them and selecting a new node.
There is another solution, however, and it involves the cluster.exe command.
1. Open up a command prompt.
2. Run the following command: cluster.exe GROUP "Available Storage" /Move
Voila! The disks moved back to the other node and the virtual machine state in Hyper-V manager changed from "Saved-Critical" to "Off." I was then able to cluster the machines normally through Failover Clustering.
I attempted to start them, but received an eror that the saved state could not be restored. I attempted to delete the saved state, but received an "Unable to perform operation" error. Additionally, I could not view the properties of the virtual machines in the Saved-Critical state.
I opened up Failover Cluster manager and noticed that the storage was now owned by the other cluster node. The problem is now obvious--the storage is no longer being presented to the host on which I was configuring the virtual machines. So, how to move these disks? Since the disks are marked "Available" (not having run through the new service Failover Clustering wizard to make the virtual machines highly available), I can't move them by right-clicking on them and selecting a new node.
There is another solution, however, and it involves the cluster.exe command.
1. Open up a command prompt.
2. Run the following command: cluster.exe GROUP "Available Storage" /Move
Voila! The disks moved back to the other node and the virtual machine state in Hyper-V manager changed from "Saved-Critical" to "Off." I was then able to cluster the machines normally through Failover Clustering.
Topics:
clustering,
hyper-v,
hyper-v r2,
troubleshooting,
windows 2008 r2
Tuesday, September 28, 2010
How to Expand a Virtual Disk on the Dell MD3000i
I recently found myself in the position of having to expand a virtual disk on a Dell MD3000i. The Dell MD3000i is a great entry-point SAN, but the GUI lacks some of the functions that you think would be there (such as online volume growth).
The feat, however, can be accomplished. It just requires using the arcane command-line interface.
1. Log into the MDSM GUI and make sure no other operations are currently in progress (disk initialization, rebuild, etc). You can find this information on the Summary tab under Operations in Progress.
2. Note the virtual disk name that you want to expand (such as server_a_vol_1). To see a list of your virtual disks from the GUI, click on the Summary tab and then the Disk Groups & Virtual Disks link.
3. Note the name of the array. You can find this information on gray menu bar above the tabs.
4. Exit the MDSM GUI.
5. Open a command prompt and navigate to the directory where the MD storage software is installed (for the newer versions, the default location is C:\Program Files (x86)\Dell\MD Storage Manager\client on x64 platforms or C:\Program Files\Dell\MD Storage Manager\client on x86 platforms).
6. Run the command:
smcli -n arrayname -c "set virtualDisk [\"virtual disk name\"] addCapacity=n;"
Where:
arrayname is the name of the storage array
virtual disk name is the name of the virtual disk
n is the capacity in bytes to add (to convert GB to bytes, multiply the number in GB by 1073741824)
For example, if you want to add 50GB to the virtual disk server_a_vol_1 on the MD3000i array named production, you would type the following:
smcli -n production -c "set virtualDisk [\"server_a_vol_1\"] addCapacity=53687091200;"
From the Windows side, the LUN will not show up as its new size until the operation is complete. The volume growth process doesn't tack on space to the end of the volume, rather, it appears to move the volume to the end and then append the storage. For newly created volumes with no data, it is much faster to destroy the LUN and recreate it than to go through an online expansion. If the volume has data on it, though, you are left with little option.
Once the operation is complete, you can expand the volume using either the disk management snap-in (diskmgmt.msc) or diskpart.exe.
The feat, however, can be accomplished. It just requires using the arcane command-line interface.
1. Log into the MDSM GUI and make sure no other operations are currently in progress (disk initialization, rebuild, etc). You can find this information on the Summary tab under Operations in Progress.
2. Note the virtual disk name that you want to expand (such as server_a_vol_1). To see a list of your virtual disks from the GUI, click on the Summary tab and then the Disk Groups & Virtual Disks link.
3. Note the name of the array. You can find this information on gray menu bar above the tabs.
4. Exit the MDSM GUI.
5. Open a command prompt and navigate to the directory where the MD storage software is installed (for the newer versions, the default location is C:\Program Files (x86)\Dell\MD Storage Manager\client on x64 platforms or C:\Program Files\Dell\MD Storage Manager\client on x86 platforms).
6. Run the command:
smcli -n arrayname -c "set virtualDisk [\"virtual disk name\"] addCapacity=n;"
Where:
arrayname is the name of the storage array
virtual disk name is the name of the virtual disk
n is the capacity in bytes to add (to convert GB to bytes, multiply the number in GB by 1073741824)
For example, if you want to add 50GB to the virtual disk server_a_vol_1 on the MD3000i array named production, you would type the following:
smcli -n production -c "set virtualDisk [\"server_a_vol_1\"] addCapacity=53687091200;"
From the Windows side, the LUN will not show up as its new size until the operation is complete. The volume growth process doesn't tack on space to the end of the volume, rather, it appears to move the volume to the end and then append the storage. For newly created volumes with no data, it is much faster to destroy the LUN and recreate it than to go through an online expansion. If the volume has data on it, though, you are left with little option.
Once the operation is complete, you can expand the volume using either the disk management snap-in (diskmgmt.msc) or diskpart.exe.
Monday, September 20, 2010
Outlook 2007 Continuously Prompting for POP3 Credentials
Recently, I had a customer running Outlook 2007 on Windows 7 that experienced a condition I like to refer to as "the dreaded attack of the authentication dialog box." She was connecting to a POP3 server and had the "Save password" box checked, but during every Send/Receive session, would get prompted twice for credentials.
The solution was simple, but elusive.
1. Close Outlook.
2. Open Windows Explorer.
3. Tools > Folder Options > View; click "Show hidden files, folders, and drives."
4. Deselect "Hid protected operating system files (Recommended)" and click OK.
5. Navigate to %USERPROFILE%\AppData\Roaming\Microsoft\Protect.
6. Rename the folder S-1-5-21- to S-1-5-21--old.
7. Rename the file CREDHIST to CREDHIST-old.
8. Restart.
9. Launch Outlook, enter credentials when prompted, and click Save Password.
The solution was simple, but elusive.
1. Close Outlook.
2. Open Windows Explorer.
3. Tools > Folder Options > View; click "Show hidden files, folders, and drives."
4. Deselect "Hid protected operating system files (Recommended)" and click OK.
5. Navigate to %USERPROFILE%\AppData\Roaming\Microsoft\Protect.
6. Rename the folder S-1-5-21-
7. Rename the file CREDHIST to CREDHIST-old.
8. Restart.
9. Launch Outlook, enter credentials when prompted, and click Save Password.
Tuesday, September 7, 2010
General Authentication Failed when using IMAP over SSL on Exchange 2010
Ran into an interesting certificate issue with Exchange 2010 and wildcard certificates.
I had installed a wildcard certificate for our domain on an Exchange 2010 server (just like I had previously for Exchange 2007) and enabled the IMAP service (Microsoft Exchange IMAP4 is the Exchange 2010 name of the service). However, when running the Enable-ExchangeCertificate cmdlet, I received an error enabling the wildcard certificate for IMAP services.
I eventually stumbled across this KB Article, Certificates that contain wildcard characters may not work correctly on an Exchange 2007 Service Pack 1-based server. When I ran the Get-ImapSettings cmdlet, I received the following output:
UnencryptedorTLSBindings SSLBindings LoginType X509CertificateName
------------------------ ----------- --------- -------------------
{:::143, 0.0.0.0:143} {:::993, 0.0.0.0:993} SecureLogin myservername
According to the KB, this is due to a problem with the way the cmdlet generates the X.509 certificate name. It can't interpret the wildcard character correctly, so it says that the FQDN of your server is just the NetBIOS name of your server. Oops. Exchange 2007 SP1 Roll-Up 4 is supposed to fix this behavior, but I experienced it on an Exchange 2010 server that was updated to current before deploying the certificate.
After I updated the X.509 Certificate name (using the command Set-ImapSettings -X509CertificateName "myserver.mydomain.com"), I restarted the IMAP service.
To make sure everything was working, I configured an Outlook profile with the IMAP settings of my test mailbox. When I clicked the "Test Connection" button, I was greeted with yet another error:
The answer, was, in fact, in the output of the Get-ImapSettings cmdlet that I previously ran. Apparently, it was looking for a secure login method. However, in most SSL-enabled configurations, data is submitted in clear text through the SSL tunnel. To test my theory, I ran the command Set-ImapSettings -LoginType PlainTextlogin and restarted the IMAP service again. In my Outlook client, I clicked the "Test Connection" button again and all was right with the world.
I had installed a wildcard certificate for our domain on an Exchange 2010 server (just like I had previously for Exchange 2007) and enabled the IMAP service (Microsoft Exchange IMAP4 is the Exchange 2010 name of the service). However, when running the Enable-ExchangeCertificate cmdlet, I received an error enabling the wildcard certificate for IMAP services.
I eventually stumbled across this KB Article, Certificates that contain wildcard characters may not work correctly on an Exchange 2007 Service Pack 1-based server. When I ran the Get-ImapSettings cmdlet, I received the following output:
UnencryptedorTLSBindings SSLBindings LoginType X509CertificateName
------------------------ ----------- --------- -------------------
{:::143, 0.0.0.0:143} {:::993, 0.0.0.0:993} SecureLogin myservername
According to the KB, this is due to a problem with the way the cmdlet generates the X.509 certificate name. It can't interpret the wildcard character correctly, so it says that the FQDN of your server is just the NetBIOS name of your server. Oops. Exchange 2007 SP1 Roll-Up 4 is supposed to fix this behavior, but I experienced it on an Exchange 2010 server that was updated to current before deploying the certificate.
After I updated the X.509 Certificate name (using the command Set-ImapSettings -X509CertificateName "myserver.mydomain.com"), I restarted the IMAP service.
To make sure everything was working, I configured an Outlook profile with the IMAP settings of my test mailbox. When I clicked the "Test Connection" button, I was greeted with yet another error:
Log on to incoming mail server (IMAP): General authentication failed. None of the authentication methods supported by your IMAP server (if any) are supported on this computer.
The answer, was, in fact, in the output of the Get-ImapSettings cmdlet that I previously ran. Apparently, it was looking for a secure login method. However, in most SSL-enabled configurations, data is submitted in clear text through the SSL tunnel. To test my theory, I ran the command Set-ImapSettings -LoginType PlainTextlogin and restarted the IMAP service again. In my Outlook client, I clicked the "Test Connection" button again and all was right with the world.
Thursday, April 15, 2010
Emailreg.org is a scam
Barracuda ... The mere mention of their name strikes fear in the hearts of any email admin unlucky enough to have to do relay mail through one of their devices.
One of my customers today submitted a ticket with problems relaying mail to one of their customers using a Barracuda device. My customer's relay responds with this message:
Ah, yes, the Barracuda Black List. Clicking on the link they provide takes you do a page where they tell you, "Sorry, your email was blocked....Barracuda Networks is not attempting to block your individual emails in particular. The repuation systemed uses automated algorithms for determining its results -- very similar to the anti-fraud mechanisms used for credit cards."
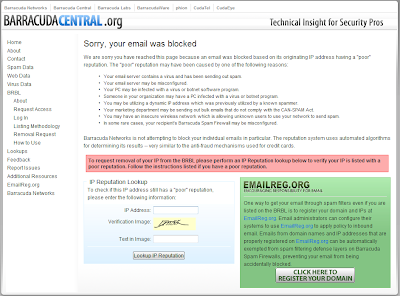
Yeah, whatever. You can put any IP address in the URL, and it will give you the same message for each one. It's a generic page they use to try to get you to buy into their Emailreg.org scam.
Clicking on the "Click here to register your domain" link and you have the ability to sign up and register your domains. Sounds great, right? Except for the $20 USD fee per domain registered.
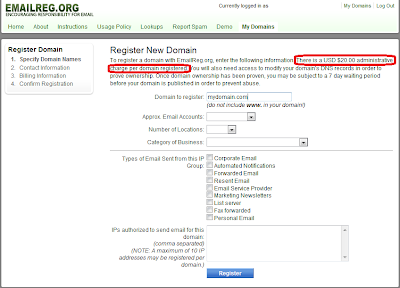
For a while, Barracuda Networks denied that they had anything to do with Emailreg.org and said that they only used the list provided there to help determine what mail was spam. And, if you queried emailreg.org for the WHOIS information, it's obscured, so it's hard to know:
Domain ID:D152388600-LROR
Domain Name:EMAILREG.ORG
Created On:12-Apr-2008 21:40:49 UTC
Last Updated On:14-Mar-2010 12:46:16 UTC
Expiration Date:12-Apr-2011 21:40:49 UTC
Sponsoring Registrar:eNom, Inc. (R39-LROR)
Status:CLIENT TRANSFER PROHIBITED
Registrant ID:77b4c5687ae40560
Registrant Name:Whois Agent
Registrant Organization:Whois Privacy Protection Service, Inc.
Registrant Street1:PMB 368, 14150 NE 20th St - F1
Registrant Street2:
Registrant Street3:
Registrant City:Bellevue
Registrant State/Province:WA
Registrant Postal Code:98007
Registrant Country:US
Registrant Phone:+1.4252740657
Registrant Phone Ext.:
Registrant FAX:
Registrant FAX Ext.:
Registrant Email:tsbnwxhk@whoisprivacyprotect.com
Admin ID:77b4c5687ae40560
Admin Name:Whois Agent
Admin Organization:Whois Privacy Protection Service, Inc.
Admin Street1:PMB 368, 14150 NE 20th St - F1
Admin Street2:
Admin Street3:
Admin City:Bellevue
Admin State/Province:WA
Admin Postal Code:98007
Admin Country:US
Admin Phone:+1.4252740657
Admin Phone Ext.:
Admin FAX:
Admin FAX Ext.:
Admin Email:tsbnwxhk@whoisprivacyprotect.com
Tech ID:77b4c5687ae40560
Tech Name:Whois Agent
Tech Organization:Whois Privacy Protection Service, Inc.
Tech Street1:PMB 368, 14150 NE 20th St - F1
Tech Street2:
Tech Street3:
Tech City:Bellevue
Tech State/Province:WA
Tech Postal Code:98007
Tech Country:US
Tech Phone:+1.4252740657
Tech Phone Ext.:
Tech FAX:
Tech FAX Ext.:
Tech Email:tsbnwxhk@whoisprivacyprotect.com
Name Server:NS2.MYDYNDNS.ORG
Name Server:NS1.MYDYNDNS.ORG
Name Server:NS3.MYDYNDNS.ORG
Name Server:NS4.MYDYNDNS.ORG
Name Server:NS5.MYDYNDNS.ORG
Name Server:
Name Server:
Name Server:
Name Server:
Name Server:
Name Server:
Name Server:
Name Server:
DNSSEC:Unsigned
But alas, IP address information is not hidden from ARIN:
Network Information for: 64.235.146.64
--------------------------------------------------------------
OrgName: Barracuda Networks, Inc.
OrgID: BARRA-7
Address: 3175 S. Winchester Blvd
City: Campbell
StateProv: CA
PostalCode: 95008
Country: US
NetRange: 64.235.144.0 - 64.235.159.255
CIDR: 64.235.144.0/20
OriginAS: AS15324
NetName: BARRAUCDA
NetHandle: NET-64-235-144-0-1
Parent: NET-64-0-0-0-0
NetType: Direct Assignment
NameServer: NS1.P23.DYNECT.NET
NameServer: NS2.P23.DYNECT.NET
NameServer: NS3.P23.DYNECT.NET
NameServer: NS4.P23.DYNECT.NET
Comment: http://www.barracuda.com/
RegDate: 2006-10-31
Updated: 2010-03-04
RAbuseHandle: BARRA1-ARIN
RAbuseName: Barracuda Hostmaster
RAbusePhone: +1-408-342-5400
RAbuseEmail: hostmaster@barracuda.com
RNOCHandle: BARRA1-ARIN
RNOCName: Barracuda Hostmaster
RNOCPhone: +1-408-342-5400
RNOCEmail: hostmaster@barracuda.com
RTechHandle: BARRA1-ARIN
RTechName: Barracuda Hostmaster
RTechPhone: +1-408-342-5400
RTechEmail: hostmaster@barracuda.com
OrgTechHandle: BARRA1-ARIN
OrgTechName: Barracuda Hostmaster
OrgTechPhone: +1-408-342-5400
OrgTechEmail: hostmaster@barracuda.com
# ARIN WHOIS database, last updated 2010-04-14 20:00
# Enter ? for additional hints on searching ARIN's WHOIS database.
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at https://www.arin.net/whois_tou.html
Sneaky. But, that's the way Barracuda is.
Thankfully, there's another way, although Barracuda devices may or may not look at it (I've not confirmed it either way). The method is called Sender Policy Framework, and it's free. The Sender Policy Framework relies on a DNS record to check which hosts are "permitted" to send email for a particular domain. Check out http://www.openspf.org for a wizard to help create your SPF record.
One of my customers today submitted a ticket with problems relaying mail to one of their customers using a Barracuda device. My customer's relay responds with this message:
#554 Service unavailable; Client host [XXXXXXXXXX.XXXXXXX.XXX] blocked using Barracuda Reputation; http://bbl.barracudacentral.com/q.cgi?ip=XXX.XXX.XXX.XXX ##
Ah, yes, the Barracuda Black List. Clicking on the link they provide takes you do a page where they tell you, "Sorry, your email was blocked....Barracuda Networks is not attempting to block your individual emails in particular. The repuation systemed uses automated algorithms for determining its results -- very similar to the anti-fraud mechanisms used for credit cards."

Yeah, whatever. You can put any IP address in the URL, and it will give you the same message for each one. It's a generic page they use to try to get you to buy into their Emailreg.org scam.
Clicking on the "Click here to register your domain" link and you have the ability to sign up and register your domains. Sounds great, right? Except for the $20 USD fee per domain registered.

For a while, Barracuda Networks denied that they had anything to do with Emailreg.org and said that they only used the list provided there to help determine what mail was spam. And, if you queried emailreg.org for the WHOIS information, it's obscured, so it's hard to know:
Domain ID:D152388600-LROR
Domain Name:EMAILREG.ORG
Created On:12-Apr-2008 21:40:49 UTC
Last Updated On:14-Mar-2010 12:46:16 UTC
Expiration Date:12-Apr-2011 21:40:49 UTC
Sponsoring Registrar:eNom, Inc. (R39-LROR)
Status:CLIENT TRANSFER PROHIBITED
Registrant ID:77b4c5687ae40560
Registrant Name:Whois Agent
Registrant Organization:Whois Privacy Protection Service, Inc.
Registrant Street1:PMB 368, 14150 NE 20th St - F1
Registrant Street2:
Registrant Street3:
Registrant City:Bellevue
Registrant State/Province:WA
Registrant Postal Code:98007
Registrant Country:US
Registrant Phone:+1.4252740657
Registrant Phone Ext.:
Registrant FAX:
Registrant FAX Ext.:
Registrant Email:tsbnwxhk@whoisprivacyprotect.com
Admin ID:77b4c5687ae40560
Admin Name:Whois Agent
Admin Organization:Whois Privacy Protection Service, Inc.
Admin Street1:PMB 368, 14150 NE 20th St - F1
Admin Street2:
Admin Street3:
Admin City:Bellevue
Admin State/Province:WA
Admin Postal Code:98007
Admin Country:US
Admin Phone:+1.4252740657
Admin Phone Ext.:
Admin FAX:
Admin FAX Ext.:
Admin Email:tsbnwxhk@whoisprivacyprotect.com
Tech ID:77b4c5687ae40560
Tech Name:Whois Agent
Tech Organization:Whois Privacy Protection Service, Inc.
Tech Street1:PMB 368, 14150 NE 20th St - F1
Tech Street2:
Tech Street3:
Tech City:Bellevue
Tech State/Province:WA
Tech Postal Code:98007
Tech Country:US
Tech Phone:+1.4252740657
Tech Phone Ext.:
Tech FAX:
Tech FAX Ext.:
Tech Email:tsbnwxhk@whoisprivacyprotect.com
Name Server:NS2.MYDYNDNS.ORG
Name Server:NS1.MYDYNDNS.ORG
Name Server:NS3.MYDYNDNS.ORG
Name Server:NS4.MYDYNDNS.ORG
Name Server:NS5.MYDYNDNS.ORG
Name Server:
Name Server:
Name Server:
Name Server:
Name Server:
Name Server:
Name Server:
Name Server:
DNSSEC:Unsigned
But alas, IP address information is not hidden from ARIN:
Network Information for: 64.235.146.64
--------------------------------------------------------------
OrgName: Barracuda Networks, Inc.
OrgID: BARRA-7
Address: 3175 S. Winchester Blvd
City: Campbell
StateProv: CA
PostalCode: 95008
Country: US
NetRange: 64.235.144.0 - 64.235.159.255
CIDR: 64.235.144.0/20
OriginAS: AS15324
NetName: BARRAUCDA
NetHandle: NET-64-235-144-0-1
Parent: NET-64-0-0-0-0
NetType: Direct Assignment
NameServer: NS1.P23.DYNECT.NET
NameServer: NS2.P23.DYNECT.NET
NameServer: NS3.P23.DYNECT.NET
NameServer: NS4.P23.DYNECT.NET
Comment: http://www.barracuda.com/
RegDate: 2006-10-31
Updated: 2010-03-04
RAbuseHandle: BARRA1-ARIN
RAbuseName: Barracuda Hostmaster
RAbusePhone: +1-408-342-5400
RAbuseEmail: hostmaster@barracuda.com
RNOCHandle: BARRA1-ARIN
RNOCName: Barracuda Hostmaster
RNOCPhone: +1-408-342-5400
RNOCEmail: hostmaster@barracuda.com
RTechHandle: BARRA1-ARIN
RTechName: Barracuda Hostmaster
RTechPhone: +1-408-342-5400
RTechEmail: hostmaster@barracuda.com
OrgTechHandle: BARRA1-ARIN
OrgTechName: Barracuda Hostmaster
OrgTechPhone: +1-408-342-5400
OrgTechEmail: hostmaster@barracuda.com
# ARIN WHOIS database, last updated 2010-04-14 20:00
# Enter ? for additional hints on searching ARIN's WHOIS database.
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at https://www.arin.net/whois_tou.html
Sneaky. But, that's the way Barracuda is.
Thankfully, there's another way, although Barracuda devices may or may not look at it (I've not confirmed it either way). The method is called Sender Policy Framework, and it's free. The Sender Policy Framework relies on a DNS record to check which hosts are "permitted" to send email for a particular domain. Check out http://www.openspf.org for a wizard to help create your SPF record.
Wednesday, April 7, 2010
Windows 2008 Hyper-V R2 Background Merge
When you remove a snapshot or snapshot subtree from a Hyper-V VM, there is a merge process that combines the data in the .avhd snapshot file back into the VM's VHD.
In Windows 2008 RTM, the merge process only happened once the virtual machine was shut down. The VM was unavailable for the duration of this process. There was, however, a progress bar displayed in either SCVMM or Hyper-V Manager that would indicate the completion percentage.
In Windows 2008 R2, however, the merge process happens in the background. Any indication of it happening is no longer easily visible in the console.
To view the progress of a merge, run the following PowerShell command:
This will give you output about all merges happening, the elasped time (in seconds, so be prepared to do some math), as well as the job completion percentage.
In Windows 2008 RTM, the merge process only happened once the virtual machine was shut down. The VM was unavailable for the duration of this process. There was, however, a progress bar displayed in either SCVMM or Hyper-V Manager that would indicate the completion percentage.
In Windows 2008 R2, however, the merge process happens in the background. Any indication of it happening is no longer easily visible in the console.
To view the progress of a merge, run the following PowerShell command:
Get-WmiObject -Namespace "root\virtualization" -Query "select * from Msvm_ConcreteJob" | Where {$_.ElementName -eq 'Merge in Progress'}
This will give you output about all merges happening, the elasped time (in seconds, so be prepared to do some math), as well as the job completion percentage.
Thursday, February 11, 2010
Troubleshooting WinSXS (Side-by-Side) problems
While attempting to run a newly-installed OmniPage Pro 17 on a Windows 2008 x64 machine, I received a cryptic and frustrating error:
The application has failed to start because its side-by-side configuration is incorrect. Please see the application log for more details.
So, what do I do? I try re-running it. I try removing and reinstalling it. I run a repair from the Programs and Features Control Panel Applet. Nothing seems to be yielding any results.
So, I decide to check out the Application Log, like the dialog box suggested.
The Application Event Log has a little more detail about what's missing:
Activation context generation failed for "C:\Program Files (x86)\Nuance\OmniPage17\OmniPage17.exe". Dependent Assembly Microsoft.VC80.MFC,processorArchitecture="x86",publicKeyToken="1fc8b3b9a1e18e3b",type="win32",version="8.0.50727.762" could not be found. Please use sxstrace.exe for detailed diagnosis.
So, I crack open a command prompt and run the following command:
sxstrace trace -logfile:omnipage.etl
The system returns the following message:
Tracing started. Trace will be saved to file omnipage.etl.
Press Enter to stop tracing...
I launch the application again, generate the error, tab back to the command prompt window, and then press Enter to stop tracing.
You can try to read the trace file, but it's not going to do you any good. You need to convert it to human-readable form with the following command:
sxstrace parse -logfile:omnipage.etl -outfile:omnipage.txt
After a few moments, you should receive a notification that it's complete:
Parsing log file omnipage.etl...
Parsing finished! Output saved to file omnipage.txt.
At that point, you can open up the result file (omnipage.txt in my case) to get a detailed analysis of what is wrong.
=================
Begin Activation Context Generation.
Input Parameter:
Flags = 0
ProcessorArchitecture = Wow32
CultureFallBacks = en-US;en
ManifestPath = C:\Program Files (x86)\Nuance\OmniPage17\OmniPage17.exe
AssemblyDirectory = C:\Program Files (x86)\Nuance\OmniPage17\
Application Config File =
-----------------
INFO: Parsing Manifest File C:\Program Files (x86)\Nuance\OmniPage17\OmniPage17.exe.
INFO: Manifest Definition Identity is (null).
INFO: Reference: Microsoft.VC80.CRT,processorArchitecture="x86",publicKeyToken="1fc8b3b9a1e18e3b",type="win32",version="8.0.50727.762"
INFO: Reference: Microsoft.VC80.MFC,processorArchitecture="x86",publicKeyToken="1fc8b3b9a1e18e3b",type="win32",version="8.0.50727.762"
INFO: Reference: Microsoft.Windows.Common-Controls,language="*",processorArchitecture="x86",publicKeyToken="6595b64144ccf1df",type="win32",version="6.0.0.0"
INFO: Resolving reference Microsoft.VC80.CRT,processorArchitecture="x86",publicKeyToken="1fc8b3b9a1e18e3b",type="win32",version="8.0.50727.762".
INFO: Resolving reference for ProcessorArchitecture WOW64.
INFO: Resolving reference for culture Neutral.
INFO: Applying Binding Policy.
INFO: No publisher policy found.
INFO: No binding policy redirect found.
INFO: Begin assembly probing.
INFO: Did not find the assembly in WinSxS.
INFO: Attempt to probe manifest at C:\Windows\assembly\GAC_32\Microsoft.VC80.CRT\8.0.50727.762__1fc8b3b9a1e18e3b\Microsoft.VC80.CRT.DLL.
INFO: Did not find manifest for culture Neutral.
INFO: End assembly probing.
The long and short of it is that OmniPage is looking for some C++ components that it can't find in the program files directory or the SxS manifest. Specifically, it can't find the x86 platform version of the C++ components. So, I download and install the Visual Studio 2005 C++ Redistributable package (which the application vendor should have bundled), and the problem is resolved.
You can download the components here:
Microsoft Visual C++ 2005 SP1 Redistributable Package (x86)
Microsoft Visual C++ 2005 SP1 Redistributable Package (x64)
The application has failed to start because its side-by-side configuration is incorrect. Please see the application log for more details.
So, what do I do? I try re-running it. I try removing and reinstalling it. I run a repair from the Programs and Features Control Panel Applet. Nothing seems to be yielding any results.
So, I decide to check out the Application Log, like the dialog box suggested.
The Application Event Log has a little more detail about what's missing:
Activation context generation failed for "C:\Program Files (x86)\Nuance\OmniPage17\OmniPage17.exe". Dependent Assembly Microsoft.VC80.MFC,processorArchitecture="x86",publicKeyToken="1fc8b3b9a1e18e3b",type="win32",version="8.0.50727.762" could not be found. Please use sxstrace.exe for detailed diagnosis.
So, I crack open a command prompt and run the following command:
sxstrace trace -logfile:omnipage.etl
The system returns the following message:
Tracing started. Trace will be saved to file omnipage.etl.
Press Enter to stop tracing...
I launch the application again, generate the error, tab back to the command prompt window, and then press Enter to stop tracing.
You can try to read the trace file, but it's not going to do you any good. You need to convert it to human-readable form with the following command:
sxstrace parse -logfile:omnipage.etl -outfile:omnipage.txt
After a few moments, you should receive a notification that it's complete:
Parsing log file omnipage.etl...
Parsing finished! Output saved to file omnipage.txt.
At that point, you can open up the result file (omnipage.txt in my case) to get a detailed analysis of what is wrong.
=================
Begin Activation Context Generation.
Input Parameter:
Flags = 0
ProcessorArchitecture = Wow32
CultureFallBacks = en-US;en
ManifestPath = C:\Program Files (x86)\Nuance\OmniPage17\OmniPage17.exe
AssemblyDirectory = C:\Program Files (x86)\Nuance\OmniPage17\
Application Config File =
-----------------
INFO: Parsing Manifest File C:\Program Files (x86)\Nuance\OmniPage17\OmniPage17.exe.
INFO: Manifest Definition Identity is (null).
INFO: Reference: Microsoft.VC80.CRT,processorArchitecture="x86",publicKeyToken="1fc8b3b9a1e18e3b",type="win32",version="8.0.50727.762"
INFO: Reference: Microsoft.VC80.MFC,processorArchitecture="x86",publicKeyToken="1fc8b3b9a1e18e3b",type="win32",version="8.0.50727.762"
INFO: Reference: Microsoft.Windows.Common-Controls,language="*",processorArchitecture="x86",publicKeyToken="6595b64144ccf1df",type="win32",version="6.0.0.0"
INFO: Resolving reference Microsoft.VC80.CRT,processorArchitecture="x86",publicKeyToken="1fc8b3b9a1e18e3b",type="win32",version="8.0.50727.762".
INFO: Resolving reference for ProcessorArchitecture WOW64.
INFO: Resolving reference for culture Neutral.
INFO: Applying Binding Policy.
INFO: No publisher policy found.
INFO: No binding policy redirect found.
INFO: Begin assembly probing.
INFO: Did not find the assembly in WinSxS.
INFO: Attempt to probe manifest at C:\Windows\assembly\GAC_32\Microsoft.VC80.CRT\8.0.50727.762__1fc8b3b9a1e18e3b\Microsoft.VC80.CRT.DLL.
INFO: Did not find manifest for culture Neutral.
INFO: End assembly probing.
The long and short of it is that OmniPage is looking for some C++ components that it can't find in the program files directory or the SxS manifest. Specifically, it can't find the x86 platform version of the C++ components. So, I download and install the Visual Studio 2005 C++ Redistributable package (which the application vendor should have bundled), and the problem is resolved.
You can download the components here:
Microsoft Visual C++ 2005 SP1 Redistributable Package (x86)
Microsoft Visual C++ 2005 SP1 Redistributable Package (x64)
Sunday, February 7, 2010
A Series of Unfortunate Events
While reading about and watching coverage of Sarah Palin's closing remarks at the Tea Party convention, I couldn't help but compare it to a car accident--you want to look away, but you can't.
While we all have the right--even duty--to criticize our leaders, I find it frustrating that she is speaks with vehemence about things of which she has little or no knowledge. Since it's now rumored that she may not have been the only one in the Governor's office, one must wonder how much of this opportunist's speech is her husband's thoughts.
Her speech was light on real details, quoting few specific policies or circumstances that she was criticizing. It's typical fiery rhetoric that panders to the audience. It's much easier to criticize than it is to offer solutions (look at this post, for example).
One of few specifics that she did mention was her perspective on trying the Christmas Day bomber in civilian courts. "Because that's not how radical Islamic extremists are looking at this. They know we're at war, and to win that war we need a commander in chief and not a professor of law standing at the lectern," she was quoted as saying.
She seems to have forgotten that under Bush, more than 200 alleged terrorists were tried and convicted in the civilian court system. Apparently, what was good for the goose isn't good for the gander. One interesting study from the Center for American Progress notes that terrorists tried in military tribunals get substantially less jail time.
In the case of Salim Hamdan, Osama bin Laden's driver, a military tribunal punished Hamdan with 5 years in prison. He was credited for time served, and only was only imprisoned for an additional 5 months after his conviction. Salim Hamdan is now running around free in Yemen. Similar is the case of David Hicks, who was convicted in a military tribunal of material support for terrorism. He now lives in Australia--a free man.
Contrast those with terrorists charged in criminal court. Ali Asad Chandia, convicted in civil criminal courts for driving a member of Pakistani extremist group Lashkar-e-Taibi from Washington National Airport and helping him ship packages containing paintball equipment back to Pakistan, was punished with 15 years in prison in 2006. John Walker Lindh, the "American Taliban," is also still serving out his 20-year sentence for providing material support to terrorists and being involved in a terrorist army faction.
Palin also made remarks criticizing President Obama for his foreign policy, stating that his policies don't recognize the true threats America faces.
Perhaps her memory needs a little jogging. There were reports all over the news from 2004 through 2006 of military leaders in Iraq begging for more troops, more armor, more weapons, and more equipment in general. And, even in 2008, well after "the surge," Gen. David McKiernan had asked for up to three additional combat brigades in Afghanistan--a request that President Bush ignored. President Obama committed 17,000 troops within two months after taking office. And, when General Stanley McChrystal asked in the now-famous "McChrystal Report" for another infusion of Troops in October 2009, Obama started preparing the citizens of the US to send more of their sons and daughters. He answered by announcing in November that he would sending an additional 34,000 troops to fulfill the General's request. It would appear (to me, at least), that President Obama takes the requests seriously and processes them in a timely fashion.
As Brad Woodhouse from the DNC was quoted in the Washington Post, "No one should take national security advice seriously from a person who told the world in 2008 that her qualifications in this area were that she could see Russia from her home state." Well played.
While in one moment calling President Obama a "charismatic guy with a teleprompter," she misspoke when reading from her notes in saying that U.S. policies might discourage those who "see Alaska as a beacon of hope" (presumably instead of America). Pot? Kettle? At least the charismatic guy can read.
The principles advocating smaller, more nimble government seem like laudable goals, but champions of this effort leave a sour taste in my mouth. If people like *that* support efforts like these, what else is lurking under the covers that I should know about?
At the end of the day, I admire grass-roots movements like the Tea Party that want to put control back in the hands of the people. While I'm not a Tea Partier, I do respect the mobilization that they have achieved. Palin was quoted as saying that the Republican party would do well to try to absorb as much of the Tea Party movement as possible. I think it would be more profitable to capture the fire into your own organization as opposed to trying to dilute your core principles to get more votes.
Many Democrats who see the Tea Party as an almost-off-the-map right organization, would welcome Palin's call to action. The truth for any party is that the more mass media coverage these growing fringe groups get, the more folks are driven to the other side.
While we all have the right--even duty--to criticize our leaders, I find it frustrating that she is speaks with vehemence about things of which she has little or no knowledge. Since it's now rumored that she may not have been the only one in the Governor's office, one must wonder how much of this opportunist's speech is her husband's thoughts.
Her speech was light on real details, quoting few specific policies or circumstances that she was criticizing. It's typical fiery rhetoric that panders to the audience. It's much easier to criticize than it is to offer solutions (look at this post, for example).
One of few specifics that she did mention was her perspective on trying the Christmas Day bomber in civilian courts. "Because that's not how radical Islamic extremists are looking at this. They know we're at war, and to win that war we need a commander in chief and not a professor of law standing at the lectern," she was quoted as saying.
She seems to have forgotten that under Bush, more than 200 alleged terrorists were tried and convicted in the civilian court system. Apparently, what was good for the goose isn't good for the gander. One interesting study from the Center for American Progress notes that terrorists tried in military tribunals get substantially less jail time.
In the case of Salim Hamdan, Osama bin Laden's driver, a military tribunal punished Hamdan with 5 years in prison. He was credited for time served, and only was only imprisoned for an additional 5 months after his conviction. Salim Hamdan is now running around free in Yemen. Similar is the case of David Hicks, who was convicted in a military tribunal of material support for terrorism. He now lives in Australia--a free man.
Contrast those with terrorists charged in criminal court. Ali Asad Chandia, convicted in civil criminal courts for driving a member of Pakistani extremist group Lashkar-e-Taibi from Washington National Airport and helping him ship packages containing paintball equipment back to Pakistan, was punished with 15 years in prison in 2006. John Walker Lindh, the "American Taliban," is also still serving out his 20-year sentence for providing material support to terrorists and being involved in a terrorist army faction.
Palin also made remarks criticizing President Obama for his foreign policy, stating that his policies don't recognize the true threats America faces.
Perhaps her memory needs a little jogging. There were reports all over the news from 2004 through 2006 of military leaders in Iraq begging for more troops, more armor, more weapons, and more equipment in general. And, even in 2008, well after "the surge," Gen. David McKiernan had asked for up to three additional combat brigades in Afghanistan--a request that President Bush ignored. President Obama committed 17,000 troops within two months after taking office. And, when General Stanley McChrystal asked in the now-famous "McChrystal Report" for another infusion of Troops in October 2009, Obama started preparing the citizens of the US to send more of their sons and daughters. He answered by announcing in November that he would sending an additional 34,000 troops to fulfill the General's request. It would appear (to me, at least), that President Obama takes the requests seriously and processes them in a timely fashion.
As Brad Woodhouse from the DNC was quoted in the Washington Post, "No one should take national security advice seriously from a person who told the world in 2008 that her qualifications in this area were that she could see Russia from her home state." Well played.
While in one moment calling President Obama a "charismatic guy with a teleprompter," she misspoke when reading from her notes in saying that U.S. policies might discourage those who "see Alaska as a beacon of hope" (presumably instead of America). Pot? Kettle? At least the charismatic guy can read.
The principles advocating smaller, more nimble government seem like laudable goals, but champions of this effort leave a sour taste in my mouth. If people like *that* support efforts like these, what else is lurking under the covers that I should know about?
At the end of the day, I admire grass-roots movements like the Tea Party that want to put control back in the hands of the people. While I'm not a Tea Partier, I do respect the mobilization that they have achieved. Palin was quoted as saying that the Republican party would do well to try to absorb as much of the Tea Party movement as possible. I think it would be more profitable to capture the fire into your own organization as opposed to trying to dilute your core principles to get more votes.
Many Democrats who see the Tea Party as an almost-off-the-map right organization, would welcome Palin's call to action. The truth for any party is that the more mass media coverage these growing fringe groups get, the more folks are driven to the other side.
Wednesday, February 3, 2010
Masterful Mojito
I like to make the kinds that people talk about. The ones that are so good, that you can't order them out any more.
As the days grow longer, my thoughts turn to summer. Yes, it's only February, but a great drink is always in season.

Masterful Mojito
1 1/2 oz Bacardi Superior Rum
1/4 oz Cointreau Orange Liqueur
3 tsp sugar
1 lime
Mint leaves
Quarter the lime. In a shaker, combine ice, Bacardi Superior, Cointreau, sugar, and the juice from one half of the lime. Shake until frosty. Gently muddle 12-14 fresh mint leaves in the bottom of a Collins glass with the juice from one lime quarter. Add 6-8 ice cubes to the glass and pour the contents of the shaker over the ice. Top off with club soda and a mint sprig and garnish with the remaining lime quarter.
Change it up a little bit by adding a splash of your favorite limoncello.
As the days grow longer, my thoughts turn to summer. Yes, it's only February, but a great drink is always in season.

Masterful Mojito
1 1/2 oz Bacardi Superior Rum
1/4 oz Cointreau Orange Liqueur
3 tsp sugar
1 lime
Mint leaves
Quarter the lime. In a shaker, combine ice, Bacardi Superior, Cointreau, sugar, and the juice from one half of the lime. Shake until frosty. Gently muddle 12-14 fresh mint leaves in the bottom of a Collins glass with the juice from one lime quarter. Add 6-8 ice cubes to the glass and pour the contents of the shaker over the ice. Top off with club soda and a mint sprig and garnish with the remaining lime quarter.
Change it up a little bit by adding a splash of your favorite limoncello.
How to change the company name displayed in Windows Small Business Server 2008 Remote Web Workplace (RWW)
I recently found myself in a place where I had misspelled the name of a company during one of the SBS Setup Wizards and could not find where to change it.
The file that needs to be modified is C:\Program Files\Windows Small Business Server\Data\RWWConfig.xml
Look for the section that says signinorgnameand change it to the correct spelling.
<?xml version="1.0" encoding="utf-8" ?>
<RWWConfig>
<fileName>RWWPluginSBS, Version=6.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35</fileName>
<className>Microsoft.WindowsServerSolutions.IWorker.RWW.RWWPluginSBS</className>
<signinOrgName>Company Name</signinOrgName>
<signinBackgroundImage>images/background.jpg</signinBackgroundImage>
<signinUserBackgroundImage />
<orgLogo />
<wssgLogo>images/RwwOemLogo.png</wssgLogo>
<readEmailIcon>images/E-mail.png</readEmailIcon>
<connectToComputerIcon>images/RemoteDesktop.png</connectToComputerIcon>
<internalWebSiteIcon>images/CompanyWeb.png</internalWebSiteIcon>
<changePasswordIcon>images/changepassword.png</changePasswordIcon>
<helpDocumentationIcon>images/Help32.png</helpDocumentationIcon>
<adminConsoleIcon>images/AdminConsole.png</adminConsoleIcon>
<helpDeskIcon>images/helpdesk.png</helpDeskIcon>
<techNetIcon>images/technet.png</techNetIcon>
<showOWALink>true</showOWALink>
<showTSLink>true</showTSLink>
<showSharepointLink>true</showSharepointLink>
<showChangePasswordLink>true</showChangePasswordLink>
<showHelpDocumentationLink>true</showHelpDocumentationLink>
<showAdminConsoleLink>true</showAdminConsoleLink>
<showHelpDeskLink>true</showHelpDeskLink>
<showWebGadget>true</showWebGadget>
<showCustomOrgLinks>true</showCustomOrgLinks>
<showCustomAdminLinks>true</showCustomAdminLinks>
</RWWConfig>
The file that needs to be modified is C:\Program Files\Windows Small Business Server\Data\RWWConfig.xml
Look for the section that says signinorgname
<?xml version="1.0" encoding="utf-8" ?>
<RWWConfig>
<fileName>RWWPluginSBS, Version=6.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35</fileName>
<className>Microsoft.WindowsServerSolutions.IWorker.RWW.RWWPluginSBS</className>
<signinOrgName>Company Name</signinOrgName>
<signinBackgroundImage>images/background.jpg</signinBackgroundImage>
<signinUserBackgroundImage />
<orgLogo />
<wssgLogo>images/RwwOemLogo.png</wssgLogo>
<readEmailIcon>images/E-mail.png</readEmailIcon>
<connectToComputerIcon>images/RemoteDesktop.png</connectToComputerIcon>
<internalWebSiteIcon>images/CompanyWeb.png</internalWebSiteIcon>
<changePasswordIcon>images/changepassword.png</changePasswordIcon>
<helpDocumentationIcon>images/Help32.png</helpDocumentationIcon>
<adminConsoleIcon>images/AdminConsole.png</adminConsoleIcon>
<helpDeskIcon>images/helpdesk.png</helpDeskIcon>
<techNetIcon>images/technet.png</techNetIcon>
<showOWALink>true</showOWALink>
<showTSLink>true</showTSLink>
<showSharepointLink>true</showSharepointLink>
<showChangePasswordLink>true</showChangePasswordLink>
<showHelpDocumentationLink>true</showHelpDocumentationLink>
<showAdminConsoleLink>true</showAdminConsoleLink>
<showHelpDeskLink>true</showHelpDeskLink>
<showWebGadget>true</showWebGadget>
<showCustomOrgLinks>true</showCustomOrgLinks>
<showCustomAdminLinks>true</showCustomAdminLinks>
</RWWConfig>
Tuesday, February 2, 2010
How to enable Outlook Logging
From time to time, we get customers complaining about Outlook POP3/SMTP problems. 99% of the time, the customer has configured Outlook incorrectly (wrong username/password, wrong server, wrong ports, etc). Enabling Outlook logging can help you make the most of your troubleshooting session.
To turn on Outlook logging:
1. Launch Outlook.
2. Navigate to Tools > Options.
3. Click the Other tab.
4. Under the General section, click the Advanced Options button.
5. Place a checkmark in the Enable logging checkbox.
6. Click OK three times, acknowledging that the settings will take effect next time you start Outlook.
7. Restart Outlook.
8. Retry the action that was causing the problem.
Now, where to find this elusive logfile?
If you're running Outlook 2000, 2002/XP, or 2003 on Windows 2000, 2003, or XP:
C:\Documents and Settings\%username%\Local Settings\Temp\OPMLOG.LOG.
If you're running Outlook 2007 on Windows 2000, 2003, or XP:
C:\Documents and Settings\%username%\Local Settings\Temp\Outlook Logging\OPMLOG.LOG.
If you're running Outlook 2007 on Windows Vista, Windows 7, or Windows 2008:
C:\Users\%username%\AppData\Local\Temp\Outlook Logging\OPMLOG.LOG.
For more information, check out the following Microsoft articles:
What is the Enable logging (troubleshooting) option?
How to enable transport logging in Outlook
To turn on Outlook logging:
1. Launch Outlook.
2. Navigate to Tools > Options.
3. Click the Other tab.
4. Under the General section, click the Advanced Options button.
5. Place a checkmark in the Enable logging checkbox.
6. Click OK three times, acknowledging that the settings will take effect next time you start Outlook.
7. Restart Outlook.
8. Retry the action that was causing the problem.
Now, where to find this elusive logfile?
If you're running Outlook 2000, 2002/XP, or 2003 on Windows 2000, 2003, or XP:
C:\Documents and Settings\%username%\Local Settings\Temp\OPMLOG.LOG.
If you're running Outlook 2007 on Windows 2000, 2003, or XP:
C:\Documents and Settings\%username%\Local Settings\Temp\Outlook Logging\OPMLOG.LOG.
If you're running Outlook 2007 on Windows Vista, Windows 7, or Windows 2008:
C:\Users\%username%\AppData\Local\Temp\Outlook Logging\OPMLOG.LOG.
For more information, check out the following Microsoft articles:
What is the Enable logging (troubleshooting) option?
How to enable transport logging in Outlook
Wednesday, January 13, 2010
I love my IPhone, but...
There are so many things from a design and features perspective that keep holding this device back (at least for me, anyway). Having owned, used, and supported numerous smart phones for the last 6 years, I can definitely see places where some improvements can be made.
Don't get me wrong--this is a good device. There are some fantastic concepts here, but even Apple needs a little help now and then.
1. I think the foremost feature missing from the IPhone is Adobe Flash. We live in a Web 2.0 world--a world depedent on interactive Flash applications. It's not like the device doesn't have the capability to run Flash--the IPhone 3GS is arguably one of the most powerful devices currently on the market. The reason is that Apple sees Flash as a competitor to its own QuickTime/h.264 technologies. Flash means that developers can bypass the App Store, which further would loosen Apple's stranglehold.
2. The next big hitter is the App Store. The App Store is one of the greatest innovations in the mobile device market--it's a place where the Microsoft Windows Mobile platform totally missed the boat. It's great to be able to go to one spot to find all of the software available for the platform. Of course, having that the *only* place from which to get content seems very restrictive and very un-internet-like.
3. Cut and paste. Yes, "Cut and Paste" now works--sort of. I can't believe the massive oversight here. Every smart platform before it had this type of "feature." I had Windows CE and Windows Mobile 2003 devices that could do this. Apple had the gall to herald it's coming to the IPhone like they'd revolutionized the market. Its implementation isn't that great (a triple-tap to select a paragraph or functionality in all Apps would be nice), so there's places where its intuitiveness could be improved.
4. Where is smart dialing? I'm spoiled as a Windows Mobile user here--the phone dialer on the IPhone is absolutely awful. Even non-smartphones have a better auto-filtering interface. Most phones filter the contact list automatically as you type in either letters or numbers. Not the IPhone. You either have to go to your contact list and search or go to the Search screen to hunt up a contact. Too many steps.
5. The ability to call someone directly from anywhere in an SMS message. It's great that I can copy the text of an SMS, but in order to initiate a phone call to someone with whom I'm texting, I need to scroll to the top of the window and press the "Call" button. Let me tap (or double-tap) the user's name anywhere in the SMS message and prompt me to call from there.
6. Select multiple messages for delete in Mail. So, I can search for messages; that's great. What if I want to mass delete all messages that meet a certain search criteria (such as a particular subject)? That would be nice. You can't even single-delete messages from a Mail search, much less select multiple messages.
7. Folder expand/collapse in Mail. As an Exchange ActiveSync user, I can see and retrieve content from any of my Outlook folders without having to individually select folders for synchronization. I dig it. But what I don't dig is the fully-expanded view of all my folders. I have about 150 folders in my Outlook tree. If I want to go to "Sent Items," it takes several swipes to get there--and then I usually have to swipe back up.
8. Speaking of Mail navigation, don't give me what appears to be a scroll/position bar on the right side of the screen when I'm scrolling through folders without the ability to click/drag it. That's just plain frustrating.
9. "Invisible" Bluetooth. While it does display a small icon next to the battery, it would be nice to see a low-power blinking LED to remind me that it's on, since a lot of my apps run full-screen and I lose the on-screen icon. All of my other phones had a little blue light that flashed whenever Bluetooth was activated. Throw a guy a bone, please, Apple.
10. Ability to password-prompt for app removal. I can't tell you how many Apps have been uninstalled inadvertently by my kids. You require a password to buy something from the App store; require one to remove the app as well.
Anyone else have features they'd like to see native to the IPhone?
Don't get me wrong--this is a good device. There are some fantastic concepts here, but even Apple needs a little help now and then.
1. I think the foremost feature missing from the IPhone is Adobe Flash. We live in a Web 2.0 world--a world depedent on interactive Flash applications. It's not like the device doesn't have the capability to run Flash--the IPhone 3GS is arguably one of the most powerful devices currently on the market. The reason is that Apple sees Flash as a competitor to its own QuickTime/h.264 technologies. Flash means that developers can bypass the App Store, which further would loosen Apple's stranglehold.
2. The next big hitter is the App Store. The App Store is one of the greatest innovations in the mobile device market--it's a place where the Microsoft Windows Mobile platform totally missed the boat. It's great to be able to go to one spot to find all of the software available for the platform. Of course, having that the *only* place from which to get content seems very restrictive and very un-internet-like.
3. Cut and paste. Yes, "Cut and Paste" now works--sort of. I can't believe the massive oversight here. Every smart platform before it had this type of "feature." I had Windows CE and Windows Mobile 2003 devices that could do this. Apple had the gall to herald it's coming to the IPhone like they'd revolutionized the market. Its implementation isn't that great (a triple-tap to select a paragraph or functionality in all Apps would be nice), so there's places where its intuitiveness could be improved.
4. Where is smart dialing? I'm spoiled as a Windows Mobile user here--the phone dialer on the IPhone is absolutely awful. Even non-smartphones have a better auto-filtering interface. Most phones filter the contact list automatically as you type in either letters or numbers. Not the IPhone. You either have to go to your contact list and search or go to the Search screen to hunt up a contact. Too many steps.
5. The ability to call someone directly from anywhere in an SMS message. It's great that I can copy the text of an SMS, but in order to initiate a phone call to someone with whom I'm texting, I need to scroll to the top of the window and press the "Call" button. Let me tap (or double-tap) the user's name anywhere in the SMS message and prompt me to call from there.
6. Select multiple messages for delete in Mail. So, I can search for messages; that's great. What if I want to mass delete all messages that meet a certain search criteria (such as a particular subject)? That would be nice. You can't even single-delete messages from a Mail search, much less select multiple messages.
7. Folder expand/collapse in Mail. As an Exchange ActiveSync user, I can see and retrieve content from any of my Outlook folders without having to individually select folders for synchronization. I dig it. But what I don't dig is the fully-expanded view of all my folders. I have about 150 folders in my Outlook tree. If I want to go to "Sent Items," it takes several swipes to get there--and then I usually have to swipe back up.
8. Speaking of Mail navigation, don't give me what appears to be a scroll/position bar on the right side of the screen when I'm scrolling through folders without the ability to click/drag it. That's just plain frustrating.
9. "Invisible" Bluetooth. While it does display a small icon next to the battery, it would be nice to see a low-power blinking LED to remind me that it's on, since a lot of my apps run full-screen and I lose the on-screen icon. All of my other phones had a little blue light that flashed whenever Bluetooth was activated. Throw a guy a bone, please, Apple.
10. Ability to password-prompt for app removal. I can't tell you how many Apps have been uninstalled inadvertently by my kids. You require a password to buy something from the App store; require one to remove the app as well.
Anyone else have features they'd like to see native to the IPhone?
Sunday, January 10, 2010
Installing Data Protection Manager 2007 on a Dell NX3000
Dell has this great NAS device that runs Windows 2008 Storage Server Standard--the NX3000. The only problem is that Dell treats it like an "appliance," meaning you can't partition it the way you want. I recently ordered two with 6x1TB drives and wanted to deploy DPM to them. Unfortunately, Dell's RAID1/RAID5 combo doesn't make very good use of the available storage. I wanted to be able to use most of the space for DPM storage, so I needed to re-set it up from scratch.
Dell only provides "recovery" media (an image as opposed to install media), so you need to obtain the Windows 2008 Storage Server media on your own (such as from MSDN). Note: Dell's recovery media will not work if the disk configuration if the first two drives are not in a mirror set.
I spent two days figuring it out so you don't have to.
Once you have the media, here are the steps to get it set up completely:
1. Download all of the drivers from the Dell Support Site and save them to a USB stick.
2. Install from Windows Storage Server 2008 media. Be sure to select the edition (if installing from media with multiple editions) that matches the WSS key on the system chassis). Use the WSS key on the chassis for installation.
3. Install drivers from USB stick.
4. Log in to server with username administrator, password wSS2008!. This would be the only OS I've ever installed with a pre-configured administrator password.
5. Install Dell OpenManage software from Dell System Build DVD.
6. Restart.
7. Add Web Server role and add all role services (except FTP).
8. Open command prompt and run start /wait ocsetup.exe SIS-Limited /norestart.
9. Run Windows Update and install all available updates to bring current.
10. Restart.
11. From System Center Data Protection Manager DVD, navigate to SQL2005 installation directory.
12. Run Setup to install SQL 2005.
13. Select Database, Reporting Services, and Workstation/Client components. Ensure all sub-items are selected by clicking "Advanced" button and expanding each component.
14. Specify an instance name of MS$DPM2007$.
15. On the Service Account page, select the Customize for each service check box and configure as follows:
a. Select Customize for each service account.
b. In the Service box, select SQL Server.
c. Select Use the built-in System account, then select Local System account.
d. In the Service box, select SQL Server Agent.
e. Select Use the built-in System account, then select Local System account.
f. In the Service box, select Reporting Services.
g. Select Use the built-in System account, and then select the Network service account.
h. In the Service box, select SQL Browser.
i. Select Use the built-in System account, then select Local Service account.
16. Accept defaults for the rest of the SQL 2005 installation.
17. Open the Internet Services Manager (Windows 2008 version).
18. Expand Web Sites, expand Default Web Site, and then click the virtual directory for the report server.
19. Under Features View, double-click Handler Mappings.
20. Under Actions, click Edit Feature Permissions.
21. Click to select the Scripts check box, and then click OK.
22. Close Internet Services Manager.
23. Open Services applet.
24. Stop all SQL services.
25. Run SQL 2005 SP2 setup.
26. Restart.
27. Launch System Center Data Protection Manager 2007 setup.
28. Select the local database instance (MS$DPM2007$).
29. Enter a strong password for the DPM account.
30. Complete setup, accepting all defaults.
31. Restart.
32. Download and install DPM 2007 SP1.
33. Restart.
34. Download and install most recent hotfixes from http://support.microsoft.com/kb/961659/EN-US.
35. Call 1-888-571-2048 (if in USA) to activate WSS by phone (online activation will most likely not work in this instance; you will need to speak to a representative).
Good luck!
Dell only provides "recovery" media (an image as opposed to install media), so you need to obtain the Windows 2008 Storage Server media on your own (such as from MSDN). Note: Dell's recovery media will not work if the disk configuration if the first two drives are not in a mirror set.
I spent two days figuring it out so you don't have to.
Once you have the media, here are the steps to get it set up completely:
1. Download all of the drivers from the Dell Support Site and save them to a USB stick.
2. Install from Windows Storage Server 2008 media. Be sure to select the edition (if installing from media with multiple editions) that matches the WSS key on the system chassis). Use the WSS key on the chassis for installation.
3. Install drivers from USB stick.
4. Log in to server with username administrator, password wSS2008!. This would be the only OS I've ever installed with a pre-configured administrator password.
5. Install Dell OpenManage software from Dell System Build DVD.
6. Restart.
7. Add Web Server role and add all role services (except FTP).
8. Open command prompt and run start /wait ocsetup.exe SIS-Limited /norestart.
9. Run Windows Update and install all available updates to bring current.
10. Restart.
11. From System Center Data Protection Manager DVD, navigate to SQL2005 installation directory.
12. Run Setup to install SQL 2005.
13. Select Database, Reporting Services, and Workstation/Client components. Ensure all sub-items are selected by clicking "Advanced" button and expanding each component.
14. Specify an instance name of MS$DPM2007$.
15. On the Service Account page, select the Customize for each service check box and configure as follows:
a. Select Customize for each service account.
b. In the Service box, select SQL Server.
c. Select Use the built-in System account, then select Local System account.
d. In the Service box, select SQL Server Agent.
e. Select Use the built-in System account, then select Local System account.
f. In the Service box, select Reporting Services.
g. Select Use the built-in System account, and then select the Network service account.
h. In the Service box, select SQL Browser.
i. Select Use the built-in System account, then select Local Service account.
16. Accept defaults for the rest of the SQL 2005 installation.
17. Open the Internet Services Manager (Windows 2008 version).
18. Expand Web Sites, expand Default Web Site, and then click the virtual directory for the report server.
19. Under Features View, double-click Handler Mappings.
20. Under Actions, click Edit Feature Permissions.
21. Click to select the Scripts check box, and then click OK.
22. Close Internet Services Manager.
23. Open Services applet.
24. Stop all SQL services.
25. Run SQL 2005 SP2 setup.
26. Restart.
27. Launch System Center Data Protection Manager 2007 setup.
28. Select the local database instance (MS$DPM2007$).
29. Enter a strong password for the DPM account.
30. Complete setup, accepting all defaults.
31. Restart.
32. Download and install DPM 2007 SP1.
33. Restart.
34. Download and install most recent hotfixes from http://support.microsoft.com/kb/961659/EN-US.
35. Call 1-888-571-2048 (if in USA) to activate WSS by phone (online activation will most likely not work in this instance; you will need to speak to a representative).
Good luck!
Thursday, January 7, 2010
A Long Way Home
Most bar Long Island Iced Teas are made with a mix of bottom-shelf liquors and sour mix. This one is not.
1/2 oz Tanqueray Gin
1/2 oz Cointreau Orange Liqueuer
1/2 oz 1800 Silver Tequila
1/2 oz Bacardi Superior Rum
1/2 oz Absolut Citron Vodka
1/2 oz filtered water
1 Lemon
3 tsp sugar
Coca-Cola, Royal Crown, or other cola with a sweet aftertaste
Fill a shaker with fresh cracked ice and add all alcohols, water, and sugar. Cut lemon in half; squeeze one half into the shaker. Shake vigorously and strain into ice-filled glass. Top with Coca-cola or RC until it is the color of traditional iced tea. Cut the remaining lemon half in half and garnish drink.

1/2 oz Tanqueray Gin
1/2 oz Cointreau Orange Liqueuer
1/2 oz 1800 Silver Tequila
1/2 oz Bacardi Superior Rum
1/2 oz Absolut Citron Vodka
1/2 oz filtered water
1 Lemon
3 tsp sugar
Coca-Cola, Royal Crown, or other cola with a sweet aftertaste
Fill a shaker with fresh cracked ice and add all alcohols, water, and sugar. Cut lemon in half; squeeze one half into the shaker. Shake vigorously and strain into ice-filled glass. Top with Coca-cola or RC until it is the color of traditional iced tea. Cut the remaining lemon half in half and garnish drink.

Subscribe to:
Posts (Atom)

